‘Although rivaled closely by SATAN PUT THE DINO BONES THERE, QUENTIN.’ –Malcolm Harris

Worst Companies At Protecting User Privacy: Skype, Verizon, Yahoo!, At&T, Apple, Microsoft.
photos { Marlo Pascual | Sean and Seng }

Worst Companies At Protecting User Privacy: Skype, Verizon, Yahoo!, At&T, Apple, Microsoft.
photos { Marlo Pascual | Sean and Seng }
One of the more memorable encounters in the history of modern art occurred late in 1961 when the period’s preeminent avant-garde dealer, Leo Castelli, paid a call at the Upper East Side Manhattan townhouse-cum-studio of Andy Warhol, whose pioneering Pop paintings based on cartoon characters including Dick Tracy, the Little King, Nancy, Popeye, and Superman had caught the eye of Castelli’s gallery director, Ivan Karp, who in turn urged his boss to go have a look for himself. Warhol, eager to make the difficult leap from commercial artist to “serious” painter, decades later recalled his crushing disappointment when Castelli coolly told him, “Well, it’s unfortunate, the timing, because I just took on Roy Lichtenstein, and the two of you in the same gallery would collide.”
Although Lichtenstein, then a thirty-eight-year-old assistant art professor at Rutgers University’s Douglass College in New Jersey, was also making pictures based on comic-book prototypes—an example of wholly independent multiple discovery not unlike such scientific findings as calculus, oxygen, photography, and evolution—he and Warhol were in fact doing quite different things with similar source material, as the divergent tangents of their later careers would amply demonstrate. By 1964, Castelli recognized his mistake and added the thwarted aspirant to his gallery roster, though not before Warhol forswore cartoon imagery, fearful of seeming to imitate Lichtenstein, of whom he always remained somewhat in awe.
In fact, what Lichtenstein and his five-years-younger contemporary Warhol had most in common was being the foremost exemplars of Cool among their generation of American visual artists. The first half of the 1960s was the apogee of what might be termed the Age of Cool—as defined by that quality of being simultaneously with-it and disengaged, in control but nonchalant, knowing but ironically self-aware, and above all inscrutably undemonstrative.

Over the past half-century, pop hits have become longer, slower and sadder, and they increasingly convey “mixed emotional cues,” according to a study just published in the journal Psychology of Aesthetics, Creativity and the Arts.
“As the lyrics of popular music became more self-focused and negative over time, the music itself became sadder-sounding and more emotionally ambiguous,” according to psychologist E. Glenn Schellenberg and sociologist Christian von Scheve.
Analyzing Top 40 hits from the mid-1960s through the first decade of the 2000s, they find an increasing percentage of pop songs are written using minor modes, which most listeners—including children—associate with gloom and despair. In what may or may not be a coincidence, they also found the percentage of female artists at the top of the charts rose steadily through the 1990s before retreating a bit in the 2000s.
photo { Weegee }

From his first months in office, President Obama secretly ordered increasingly sophisticated attacks on the computer systems that run Iran’s main nuclear enrichment facilities, significantly expanding America’s first sustained use of cyberweapons, according to participants in the program.
Mr. Obama decided to accelerate the attacks — begun in the Bush administration and code-named Olympic Games — even after an element of the program accidentally became public in the summer of 2010 because of a programming error that allowed it to escape Iran’s Natanz plant and sent it around the world on the Internet. Computer security experts who began studying the worm, which had been developed by the United States and Israel, gave it a name: Stuxnet. […]
It appears to be the first time the United States has repeatedly used cyberweapons to cripple another country’s infrastructure, achieving, with computer code, what until then could be accomplished only by bombing a country or sending in agents to plant explosives. The code itself is 50 times as big as the typical computer worm, Carey Nachenberg, a vice president of Symantec, one of the many groups that have dissected the code, said at a symposium at Stanford University in April. Those forensic investigations into the inner workings of the code, while picking apart how it worked, came to no conclusions about who was responsible.
A similar process is now under way to figure out the origins of another cyberweapon called Flame that was recently discovered to have attacked the computers of Iranian officials, sweeping up information from those machines. But the computer code appears to be at least five years old, and American officials say that it was not part of Olympic Games. They have declined to say whether the United States was responsible for the Flame attack.
Soon the two countries had developed a complex worm that the Americans called “the bug.” But the bug needed to be tested. So, under enormous secrecy, the United States began building replicas of Iran’s P-1 centrifuges. […] Those first small-scale tests were surprisingly successful: the bug invaded the computers, lurking for days or weeks, before sending instructions to speed them up or slow them down so suddenly that their delicate parts, spinning at supersonic speeds, self-destructed. After several false starts, it worked. One day, toward the end of Mr. Bush’s term, the rubble of a centrifuge was spread out on the conference table in the Situation Room, proof of the potential power of a cyberweapon. The worm was declared ready to test against the real target: Iran’s underground enrichment plant. […]
The first attacks were small, and when the centrifuges began spinning out of control in 2008, the Iranians were mystified about the cause, according to intercepts that the United States later picked up. “The thinking was that the Iranians would blame bad parts, or bad engineering, or just incompetence,” one of the architects of the early attack said.
The Iranians were confused partly because no two attacks were exactly alike. Moreover, the code would lurk inside the plant for weeks, recording normal operations; when it attacked, it sent signals to the Natanz control room indicating that everything downstairs was operating normally. “This may have been the most brilliant part of the code,” one American official said.
But by the time Mr. Bush left office, no wholesale destruction had been accomplished. Meeting with Mr. Obama in the White House days before his inauguration, Mr. Bush urged him to preserve two classified programs, Olympic Games and the drone program in Pakistan. Mr. Obama took Mr. Bush’s advice. […]
An error in the code, they said, had led it to spread to an engineer’s computer when it was hooked up to the centrifuges. […] It began replicating itself all around the world. Suddenly, the code was exposed. […] Within a week, another version of the bug brought down just under 1,000 centrifuges. Olympic Games was still on. […]
American cyberattacks are not limited to Iran.
photo { Donovan Wylie }

Seventy-four percent of dog owners believe that their dogs experience guilt. […]
There is plenty of evidence for what scientists refer to as primary emotions – happiness and fear, for example – in animals. But empirical evidence for secondary emotions like jealousy, pride, and guilt, is extremely rare in the animal cognition literature. The argument usually given for this lack of evidence is that such secondary emotions seem to require a level of cognitive sophistication, particularly when it comes to self-awareness or self-consciousness, that may not exist in non-human animals.
painting { Pan Deng }
Queuing theory is the study of lines. All kinds of lines. The lines at supermarket checkouts, the lines at toll booths, the lines of people on hold waiting for someone, anyone, to pick up at the cable company’s 1-800 number. […]
Since the mid-20th century, queuing theory has been more about feelings than formulas. For example: Midcentury New York featured a rush-hour crisis—not out on the roads, but inside office tower lobbies. There weren’t enough elevators to handle the peak crowds. Complaints were mounting. “One solution would have been to dynamite the buildings and build more elevator shafts,” says Larson. “But someone figured out the real problem isn’t just the duration of a delay. It’s how you experience that duration.” Some buildings installed floor-to-ceiling mirrors near the elevators and, entertained by their own reflections and by the flirting that sometimes ensued, people stopped complaining quite as much about the wait time.
There are three givens of human nature that queuing psychologists must address: 1) We get bored when we wait in line. 2) We really hate it when we expect a short wait and then get a long one. 3) We really, really hate it when someone shows up after us but gets served before us.

“Early love is when you love the way the other person makes you feel,” explains psychiatrist Mark Goulston of the University of California, Los Angeles. “Mature love is when you love the person as he or she is.”
{ Time }
Events occurring in the brain when we are in love have similarities with mental illness.
{ BBC }
photo { Sam Hessamian }

Science-fiction writers once imagined a galactic currency that would grease the wheels of commerce from here to Alpha Centauri. In fact, however, we are tending in precisely the other direction, toward a burgeoning number of ever more specialized currencies. These will circulate electronically, by means of the mobile phones that are increasingly part of the dress of every person on the planet.
Seemingly everywhere you look, you can see the emergence of this pattern in what futurologists call the weak signals [PDF] of change. These are the changes that will be seen, a generation from now, to have foreshadowed a technological revolution. […]
In Japan and Korea, mobile phones have been used for payments for a decade, and the technology is now a standard feature there in handsets. In March, one out of six Japanese users bought something in a shop using a mobile. People also use the system to pay bills and transit fares; businesses use it to funnel loyalty rewards to customers. At first, the number of retailers accepting the new technology remained flat; once about a third of consumers were using it, though, things started to take off, producing the “hockey stick” adoption curve that we technologists love.
What’s happening in Africa is even more astonishing. Kenya is now home to the world’s most expansive mobile payments scheme, M-Pesa. […] A third of Kenya’s gross domestic product now flows through M-Pesa. […]
The rest of the world is starting to move. […] In France, mobile phone operators and banks have gotten together to launch a system for mobile proximity payments, which lets a chip-bearing platform transfer money when held close to the reader. In Germany, meanwhile, the mobile phone operators have decided to ignore the banks and go it alone. In the United States, Google is working with Sprint and MasterCard to launch Google Wallet. […]
Cash’s indirect costs are huge. […] In the United States 18 to 19 percent of total reportable income is hidden from federal tax men, a shortfall of about US $500 billion. […]
In the Netherlands, there are commercial streets that are cash free. […] In Sweden the labor unions want to remove cash from shops and banks because it is their members who get beaten and shot in robberies; the government wants to reduce the burden of police work.
photo { Marc Chaumeil }

In every economic downturn some intrepid journalist pens a story about the “Lipstick Effect” – the tendency for women to buy more beauty products when the economy is in bad shape. In theory, the behavior is driven by evolutionary concerns. With fewer men able to offer the security of financial stability, women must enhance their beauty in order to deal with the increased competition.
photo { Anthony Suau }

HorrendousRex
No one seems to have mentioned it, so I’ll point out that this looks like an M4 Carbine with iron sights, without any magazine inserted (and I have to imagine no bullet round chambered, either).
It appears to have no attachments besides the iron sights, which I thought is surprising as I thought that the foregrip and picatinny rail and ACOG scope were standard attachments for the IDF. I would imagine this is because she is a new recruit (mentioned elsewhere in the thread). [Edit: Apparently no M4 attachments are standard in the IDF, they are either soldier-purchased or disbursed for relevant combat roles.]
The gun might also be the M4A1 automatic variant of the M4, but without any modifications I don’t really know how to tell. [Apparently it might also be a short-barreled variant of the M16 - but isn’t that what an M4 is?]
The umbrella stands belong to “Carlsberg” pale lager, a product of the Carlsberg Group. Their motto is “Probably the best beer in the world”, but it is not the best beer in the world.
I’m having trouble identifying the bikinis but the girl with the gun seems to be wearing a mismatched set, as is often the fashion.
The ass is good.voodoopredatordrones
you just Sherlocked that picture…for no apparent reasonlampkyter
If he really Sherlocked it he would have told us something like how many times she’s had sex.imatosserama
I can’t definitively say how many times, or if, she has had sex. What I can say is that it is unlikely that either of the two had orgasmed earlier that day.
Look at the way they hold their hips. When a woman orgasms, there is an involuntary relaxation of several of the hip muscles. The hips are carried in a way that looks relaxed and comfortable, rather unlike the somewhat stiff postures we see here. This effect usually lasts for several hours.
Of course, they could have had sex. Quite a lot, even. But it seems unlikely that they reached an orgasm that day. I could be wrong. But it seems unlikely. A more definite conclusion could be reached if we had a video of them walking.
Edit for proof: http://www.ncbi.nlm.nih.gov/pubmed/18637995

40 Work Hacks to Improve Your Marketing Productivity
[…]
8. Communicate with teammates in person. […]
9. Use two different computers (or just different browsers) to separate distracting things like email from what you’re actively working on. […]
11. Use a Google Doc to keep a list of all your personal/work passwords handy so you can access them quickly and easily. [and SSN?][…]
14. Wear headphones without listening to music. […]
34. Adopt the “Inbox Zero” methodology, and treat your email like a to-do list.
photo { Vivian Maier }

A freak attack described as drug induced “zombie face eating” has hit international headlines this week. Until the results of a toxicological analysis emerge, the drug(s) involved is unknown and open to speculation. This has not stopped the newspapers, who understandably have gone absolutely bat-shit over the story. The Daily Mail has claimed the attacker was “high on LSD”, while the Guardian initially claimed the assailant was “under the influence of a potent LSD-like drug called bath salts”, the Guardian went on to make the bizarre claim that the assailant had taken “the delirium-inducing drug, which is similar to cocaine and other forms of LSD.” […]
Far from LSD or even formerly popular legal chemicals such as mephedrone, the consensus among speculators appears to be that the “zombie face eater” in addition to likely having an undiagnosed pre-existing mental condition may have been in a state of severe drug induced psychosis and/or may have taken something more along the lines of a PCP analogue. This is obviously pure guess work, however PCP is known for its astounding ability to precipitate psychosis, bizarre behaviour and extreme violence. It has even been linked to cases of cannibalism in the past, cases such as this are of course rare and heavily publicised but the fact that people are now taking drugs blindly as a matter of course, the contents of which may contain substances they are utterly unprepared for is extremely worrying. Another key factor pointing to PCP is that it is well known that PCP users are prone to getting naked and becoming violent. Another popular guess that may be more grounded in reality is that the drug could be MDPV, a drug with a thoroughly unpleasant reputation that has been known to be marketed as bath salts in the past.

Americans spend a ton of time commuting. According to happiness researchers, commuting is the low point of the typical day. If you look at the jobs that people actually do, though, it’s hard to understand why so many workers continue to commute. Given a computer and high-speed Internet, most desk jobs could now be done from home – or so it seems. Telecommuting wouldn’t just save workers time, frustration, and fuel; it would also let firms drastically reduce their overhead – and pass the savings along to their customers.[…]
[Alas,] workers physically commute for signaling reasons. Employers can monitor your productivity better when you actually come to the office. Workers who telecommute put themselves on the slow track to success – if they can even get hired in the first place.
photo { Michal Pudelka }

I’ve always been not only a “late adopter” but a “panicky retreater” when it comes to new media, and the something that should be said about when I first went online—which was early enough that I remember watching Web sites load as if being painted on the other side of a glass—was that I also immediately went offline. As I still often do.
photo { Vivian Maier }
Imagine someone of the type we call neurotic in common parlance. He is wiry, looks contorted, and speaks with an uneven voice. His neck moves around when he tries to express himself. When he has a small pimple his first reaction is to assume that it is cancerous, that the cancer is of the lethal type, and that it has already spread. […] In the office, he is tuned to every single possible detail, systematically transforming every molehill into a mountain. The last thing you want in life is to be in the same car with him when stuck in traffic on your way to an important appointment. The expression overreact was designed with him in mind: he does not have reactions, just overreactions.
Compare him to someone with the opposite temperament, imperturbable, with the calm under fire that is considered necessary to become a leader, military commander or a mafia godfather. Usually unruffled and immune to small information —they can impress you with their self-control in difficult circumstances. For a sample of a composed, calm and pondered voice, listen to interviews of “Sammy the Bull” Salvatore Gravano who was involved in the murder of nineteen people (all competing mobsters). He speaks with minimal effort. In the rare situations when he is angry, unlike with the neurotic fellow, everyone knows it and takes it seriously.
The supply of information to which we are exposed under modernity is transforming humans from the equable second fellow to the neurotic first. For the purpose of our discussion, the second fellow only reacts to real information, the first largely to noise. The difference between the two fellows will show us the difference between noise and signal. Noise is what you are supposed to ignore; signal what you need to heed. […]
A not well discussed property of data: it is toxic in large quantities —even in moderate quantities.
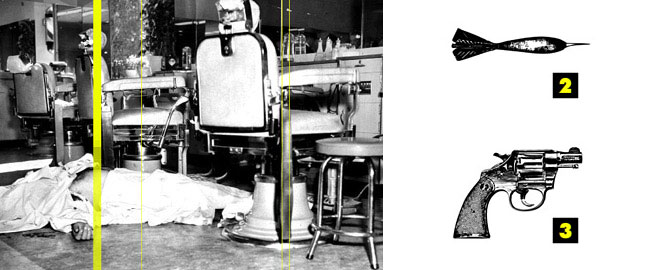
{ The publishing and design communities now know that a printed magazine can not only be used to kill at will, but as particularly efficient tool for political assassinations. | Adam Rothstein/The New Inquiry | full story }
A massive, highly sophisticated piece of malware has been newly found infecting systems in Iran and elsewhere and is believed to be part of a well-coordinated, ongoing, state-run cyberespionage operation. […] Dubbed “Flame” by Russia-based anti-virus firm Kaspersky Lab […]
The malware, which is 20 megabytes when all of its modules are installed, contains multiple libraries, SQLite3 databases, various levels of encryption — some strong, some weak — and 20 plug-ins that can be swapped in and out to provide various functionality for the attackers. It even contains some code that is written in the LUA programming language — an uncommon choice for malware.
Kaspersky Lab is calling it “one of the most complex threats ever discovered.” […]
Gostev says that because of its size and complexity, complete analysis of the code may take years. “It took us half-a-year to analyze Stuxnet,” he said. “This is 20-times more complicated. It will take us 10 years to fully understand everything.” […]
Among Flame’s many modules is one that turns on the internal microphone of an infected machine to secretly record conversations that occur either over Skype or in the computer’s near vicinity; a module that turns Bluetooth-enabled computers into a Bluetooth beacon, which scans for other Bluetooth-enabled devices in the vicinity to siphon names and phone numbers from their contacts folder; and a module that grabs and stores frequent screenshots of activity on the machine, such as instant-messaging and email communications, and sends them via a covert SSL channel to the attackers’ command-and-control servers.
The malware also has a sniffer component that can scan all of the traffic on an infected machine’s local network and collect usernames and password hashes that are transmitted across the network. The attackers appear to use this component to hijack administrative accounts and gain high-level privileges to other machines and parts of the network. […]
Because Flame is so big, it gets loaded to a system in pieces. The machine first gets hit with a 6-megabyte component, which contains about half-a-dozen other compressed modules inside. The main component extracts, decompresses and decrypts these modules and writes them to various locations on disk. The number of modules in an infection depends on what the attackers want to do on a particular machine.
Once the modules are unpacked and loaded, the malware connects to one of about 80 command-and-control domains to deliver information about the infected machine to the attackers and await further instruction from them. The malware contains a hardcoded list of about five domains, but also has an updatable list, to which the attackers can add new domains if these others have been taken down or abandoned.
While the malware awaits further instruction, the various modules in it might take screenshots and sniff the network. The screenshot module grabs desktop images every 15 seconds when a high-value communication application is being used, such as instant messaging or Outlook, and once every 60 seconds when other applications are being used.

They will be custom bugs, designer bugs — bugs that only Venter can create. He will mix them up in his private laboratory from bits and pieces of DNA, and then he will release them into the air and the water, into smokestacks and oil spills, hospitals and factories and your house.
Each of the bugs will have a mission. Some will be designed to devour things, like pollution. Others will generate food and fuel. There will be bugs to fight global warming, bugs to clean up toxic waste, bugs to manufacture medicine and diagnose disease, and they will all be driven to complete these tasks by the very fibers of their synthetic DNA.
Right now, Venter is thinking of a bug. He is thinking of a bug that could swim in a pond and soak up sunlight and urinate automotive fuel. He is thinking of a bug that could live in a factory and gobble exhaust and fart fresh air. […]
The challenge of building a synthetic bacterium from raw DNA is as byzantine as it probably sounds. It means taking four bottles of chemicals — the adenine, thymine, cytosine and guanine that make up DNA — and linking them into a daisy chain at least half a million units long, then inserting that molecule into a host cell and hoping it will spring to life as an organism that not only grows and reproduces but also manufactures exactly what its designer intended. […]
The future, he says, may be sooner than we think. Much of the groundwork is already done. In 2003, Venter’s lab used a new method to piece together a strip of DNA that was identical to a natural virus, then watched it spring to action and attack a cell. In 2008, they built a longer genome, replicating the DNA of a whole bacterium, and in 2010 they announced that they brought a bacterium with synthetic DNA to life. That organism was still mostly a copy of one in nature, but as a flourish, Venter and his team wrote their names into its DNA, along with quotes from James Joyce and J. Robert Oppenheimer and even secret messages. As the bacteria reproduced, the quotes and messages and names remained in the colony’s DNA. […]
“Agriculture as we know it needs to disappear,” Venter said. “We can design better and healthier proteins than we get from nature.” By this, he didn’t mean growing apples in a Petri dish. He meant producing bulk commodities like corn, soy and wheat, that we use in processed products like tofu and cereal. “If you can produce the key ingredients with 10 or 100 times the efficiency,” he said, “that’s a better use of land and resources.”

{ On Tuesday/Wednesday June 5/6, Earth will have the best seat — the only seat — for a great show: the Transit of Venus across the face of the Sun. | Discover | full story }
You might have seen recently that iconic retailer JC Penney is slumping badly. You almost certainly have seen the reason why: A massive, creative and aggressive new advertising and pricing campaign that promises simplified prices.
No more coupons or confusing multiple markdowns. No more 600 sales a year. No more deceptive circulars full of sneaky fine print. Heck, the store even did away with the 99 cents on the end of most price tags. Just honest, clear prices.
[…]
Shoppers hated it.