technology

It’s been a long time coming, but last night it happened: one of the greatest hackers of the 20th Century (or was it just his doppelganger?) went up against Anonymous, greatest hacktivist collective of the 21st Century. (…)
Mitnick was a legendary hacker at the dawn of the Internet and before. Convicted of wire fraud, computer fraud, and illegally intercepting a wire communication, he served nearly four years in prison. (…)
Tuesday night, he, or someone impersonating him, decided to play with Anonymous.
{ The Daily Dot | Continue reading }
photo { Daniel Ribar }
technology | March 29th, 2012 12:43 pm
showbiz, technology | March 28th, 2012 8:47 am

Who made and launched Stuxnet in the first place? Richard Clarke tells me he knows the answer.
Clarke, who served three presidents as counterterrorism czar, now operates a cybersecurity consultancy called Good Harbor. (…) We have virtually no defense against the cyberattacks that he says are targeting us now, and will be in the future. (…)
“I think it’s pretty clear that the United States government did the Stuxnet attack,” he said calmly.
{ Smithsonian | Continue reading }
previously, Stuxnet { The out-of-controller | I don’t sleep. I wait. }
illustration { Jonathan Koshi }
mystery and paranormal, technology | March 28th, 2012 8:40 am
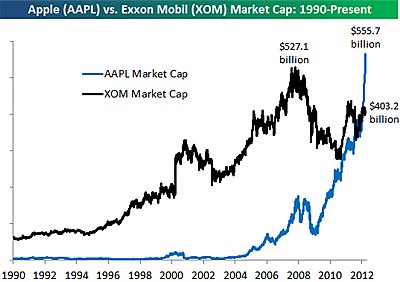
The speculation of what Apple is going to do with all their cash has long been a favorite topic in the tech and financial press. (…) What’s the point of having all that money if you’re not going to spend it?
That thinking is what we saw when Apple recently announced their cash plans. (..) “Saddened by Apple’s plan for a huge dividend. Apparently, they have nothing truly capital-intensive in the product pipeline.” (…)
Even after issuing dividends and repurchasing shares, Apple’s cash reserves will likely grow this year. They added more than $35 billion in cash and equivalents last year alone. There’s nothing “capital-intensive” that they can’t do, short of opening an Apple Store on the moon. (…)
The idea floating around before Apple’s Monday announcement that they would be buying a company like Foxconn or building factories of their own seems to make sense, since Apple is one of the more vertically integrated consumer electronics companies in the world. And they are, after all, notorious for both control and quality. But they’ve managed to lead the industry on the latter without owning a significant portion of their supply chain. (…)
Apple has this enormous negotiating power, and they use it, I am told by our sources, very aggressively to come in and basically say, “Show us your entire cost structure, every single part of what you pay and what you… and we are going to give you a razor-thin profit margin that you’re allowed to keep.
In other words: Why buy the cow?
Apple also, more importantly, finances the factories by loaning them cash and buying significant amounts of components in advance. This “Bank of Apple” strategy further establishes control over the factories, locks out competition and seems to be why competitors can’t seem to match Apple’s cost structure for products like the iPad. (…)
This brings us to those who think Apple has run out of ideas on what to do with their cash. The fevered result of this are the acquisition talks — hence the recently oft-mentioned and largely nonsensical suggestion that Apple should buy a company like Twitter. But Apple’s approach to acquisitions has always been extremely conservative, especially compared to their brethren. Since 2010 Apple’s bought a grand total of nine companies. In that same period Google has bought 52.
{ TechCrunch | Continue reading | Thanks Glenn }
related { The FBI made public a background investigation of Steve Jobs in 1991, when he was being considered by the George H. W. Bush administration for a spot on the President’s Export Council. }
economics, technology | March 28th, 2012 5:50 am

Facebook has trademarks on its name and many variations of it—including the letter “F.” The company is expanding its claim over the word “book.”
{ Ars Technica | Continue reading }
also { Facebook says it may sue employers who demand job applicants’ passwords }
social networks | March 26th, 2012 1:00 pm

Researchers have established a direct link between the number of friends you have on Facebook and the degree to which you are a “socially disruptive” narcissist, confirming the conclusions of many social media skeptics.
People who score highly on the Narcissistic Personality Inventory questionnaire had more friends on Facebook, tagged themselves more often and updated their newsfeeds more regularly.
The research comes amid increasing evidence that young people are becoming increasingly narcissistic, and obsessed with self-image and shallow friendships.
A number of previous studies have linked narcissism with Facebook use, but this is some of the first evidence of a direct relationship between Facebook friends and the most “toxic” elements of narcissistic personality disorder.
{ Guardian | Continue reading }
photo { Leo Berne }
quote { Hamilton Nolan/Gawker }
gross, ideas, psychology, social networks, technology | March 25th, 2012 11:18 am

The problem with the web is that it largely began as a world separate from meatspace. Today, most people use their real names, but this wasn’t always the case. When I started going online in the mid-90s, no one even knew my gender. I preferred that, not because I was hiding, but because I feel very strongly that I should be judged by my thoughts, not who people assume I am by seeing I am a woman, by attaching a handful of preconceived notions to what I am saying because they see my photo and think I’m too young or too old or attractive or unattractive. (…)
There is nothing wrong with wishing that it were possible to compartmentalize your digital conversations in the same way you do your meatspace exchanges. Unfortunately for us, this is not the direction the web is going, which is why pseudonymous accounts and the networks who accept them are so very, very important.
{ AV Flox | Continue reading }
image { Mark Gmehling }
experience, ideas, technology | March 23rd, 2012 11:48 am

A Star Trek-style cloaking technique allows people to spy on your Facebook account in a way that is difficult to spot and even harder to stop, say computer scientists.
{ The Physics arXiv Blog | Continue reading }
illustration { Grant Orchard }
spy & security, technology | March 22nd, 2012 3:45 pm
technology, visual design | March 22nd, 2012 7:30 am

Researchers at Yale University have developed a new way of seeing inside solid objects, including animal bones and tissues, potentially opening a vast array of dense materials to a new type of detailed internal inspection.
The technique, a novel kind of magnetic resonance imaging (MRI), creates three-dimensional images of hard and soft solids based on signals emitted by their phosphorus content.
Traditional MRI produces an image by manipulating an object’s hydrogen atoms with powerful magnets and bursts of radio waves. The atoms absorb, then emit the radio wave energy, revealing their precise location. A computer translates the radio wave signals into images. Standard MRI is a powerful tool for examining water-rich materials, such as anatomical organs, because they contain a lot of hydrogen. But it is hard to use on comparatively water-poor solids, such as bone.
The Yale team’s method targets phosphorus atoms rather than hydrogen atoms, and applies a more complicated sequence of radio wave pulses.
{ Yale News | Continue reading }
artwork { Trevor Brown, Teddy Bear Operation, 2008 }
science, technology | March 19th, 2012 5:19 pm

This has led researchers to ask the questions: How can we get mobile users to break out of their patterns, visit less frequented areas, and collect the data we need?
Researchers can’t force mobile users to behave in a certain way, but researchers at Northwestern University have found that they may be able to nudge them in the right direction by using incentives that are already part of their regular mobile routine.
“We can rely on good luck to get the data that we need,” Bustamante said, “or we can ‘soft control’ users with gaming or social network incentives to drive them where we want them.”
{ McCormick School of Engineering and Applied Science | Continue reading }
related { What Privacy Advocates Don’t Get About Data Tracking on the Web }
related { Google regularly receives requests from government agencies and courts around the world to remove content from our services and hand over user data | Who Does Facebook Think You Are Searching For? | Thanks Samantha! }
horror, spy & security, technology | March 16th, 2012 6:37 pm
asia, economics, technology, uh oh | March 16th, 2012 6:36 pm

The extraordinary ability of birds and bats to fly at speed through cluttered environments such as forests has long fascinated humans. It raises an obvious question: how do these creatures do it?
Clearly they must recognise obstacles and exercise the necessary fine control over their movements to avoid collisions while still pursuing their goal. And they must do this at extraordinary speed.
From a conventional command and control point of view, this is a hard task. Object recognition and distance judgement are both hard problems and route planning even tougher.
Even with the vast computing resources that humans have access to, it’s not at all obvious how to tackle this problem. So how flying animals manage it with immobile eyes, fixed focus optics and much more limited data processing is something of a puzzle.
Today, Ken Sebesta and John Baillieul at Boston University reveal how they’ve cracked it. These guys say that flying animals use a relatively simple algorithm to steer through clutter and that this has allowed them to derive a fundamental law that determines the limits of agile flight.
{ The Physics arXiv Blog | Continue reading }
birds, science, technology | March 16th, 2012 3:22 pm
The Moving Picture Experts Group (MPEG) is a working group of experts that was formed by ISO and IEC to set standards for audio and video compression and transmission.
It was established in 1988 by the initiative of Hiroshi Yasuda (Nippon Telegraph and Telephone) and Leonardo Chiariglione, who has been from the beginning the Chairman of the group. (…)
The MPEG compression methodology is considered asymmetric as the encoder is more complex than the decoder.
{ Wikipedia | Continue reading }
music, technology | March 16th, 2012 2:46 pm

People using Google’s email service, Gmail, on a relatively new BlackBerry smartphone may have noticed recently that some contacts now have small photos next to their names. They may have been surprised to see them there – after all, these are not photos taken by the BlackBerry itself, and its manufacturer Research In Motion has struck no data-sharing deal with Google.
Those images appear because Google has taken a profile photo users uploaded to Google+, its social network, and incorporated it into their contacts’ Gmail address book.
This is just one example of how Google is increasingly combining the information it holds about its users from its dozens of products, which range from a search engine and maps to Android smartphones, flight checkers and language translation apps.
One line in Google’s privacy policy, which came into force on Thursday, explains how it is able to do this: “If other users already have your email or other information that identifies you, we may show them your publicly visible Google Profile information, such as your name and photo.”
But when, in late January, Google published this new document detailing how it is combining the personal information it holds about its users from its dozens of different products, many privacy advocates, data protection officials and state regulators let their simmering distrust of the internet company boil over. “Google didn’t ask us if we, their customers, minded our data being merged and used in new ways,” said Jim Killock, executive director of the Open Rights Group, a digital activist. “Most people will have no choice but to put up with the change. That is wrong.”
{ FT | Continue reading }
related { How Google—and 104 Other Companies—Are Tracking Me on the Web }
google, technology | March 5th, 2012 1:15 pm
asia, relationships, technology | March 1st, 2012 3:14 pm

In this article we explore how online daters use technology to assess and manage the real and perceived risks associated with online dating. (…)
All participants believed that online dating was risky in some manner.
To manage these risks participants used technology in various ways: ways: to assist them in assessing authenticity and compatibility, to limit their self disclosure and exposure, to undertake surveillance of others and to control their online interactions. The participants made pragmatic use of the technologies available to them to minimise the risks, deploying risk management strategies throughout their online dating experiences.
{ International Journal of Emerging Technologies and Society | Continue reading }
photo { Yoshihiro Tatsuki }
relationships, technology | February 27th, 2012 12:28 pm
haha, social networks, video | February 17th, 2012 8:03 am

How would things change if Google and Bing went down for 24 hours, and there wasn’t a way around the block?
If your first thought is to do your online searches through Yahoo!, you will run into another roadblock. Since 2010, Yahoo! searches are powered by Bing. Can you name any other search engine sites off the top of your head? (…)
Losing search sites is only the tip of the iceberg. Google and Bing also provide extensive services in other areas, one of the most obvious being email—Gmail alone has 350 million users. Blacking out Gmail would certainly affect all these people, but it would also affect everyone trying to reach them.
{ Naked Capitalism | Continue reading }
Last week, I got a notice from Twitter saying the Manhattan District Attorney’s office had subpoenaed my account activity for a three-month period between September and December of last year. On October 1, I was arrested along with 700 or so other people marching across the Brooklyn Bridge as part of an early Occupy Wall Street demonstration. (…)
Why was it Twitter who got subpoenaed even though they’re my words the DA wants to see?
The short answer is: they’re not my words. Not in the legal sense at least. Part of the Twitter user agreement is that the Tweets belong to the company, not to the user. As far as the law is concerned, my online self is an informational aspect of a legal entity named Twitter, not me. That means if someone wants to use my statements against me in court, it’s not me they have to call, it’s that little blue birdie. In this context the term “microblogging” gets some new meaning: Twitter’s users really are unpaid content producers for a giant microblog hosting site.
{ Malcolm Harris/Shareable | Continue reading }
related { Will the Web Break? }
photo { Guy Bourdin }
google, technology, uh oh | February 8th, 2012 9:11 am

Facebook’s inventory of data and its revenue from advertising are small potatoes compared to some others. Google took in more than 10 times as much, with an estimated $36.5 billion in advertising revenue in 2011, by analyzing what people sent over Gmail and what they searched on the Web, and then using that data to sell ads. Hundreds of other companies have also staked claims on people’s online data by depositing software called cookies or other tracking mechanisms on people’s computers and in their browsers. If you’ve mentioned anxiety in an e-mail, done a Google search for “stress” or started using an online medical diary that lets you monitor your mood, expect ads for medications and services to treat your anxiety.
Ads that pop up on your screen might seem useful, or at worst, a nuisance. But they are much more than that. The bits and bytes about your life can easily be used against you. Whether you can obtain a job, credit or insurance can be based on your digital doppelgänger — and you may never know why you’ve been turned down.
Material mined online has been used against people battling for child custody or defending themselves in criminal cases. LexisNexis has a product called Accurint for Law Enforcement, which gives government agents information about what people do on social networks. The Internal Revenue Service searches Facebook and MySpace for evidence of tax evaders’ income and whereabouts, and United States Citizenship and Immigration Services has been known to scrutinize photos and posts to confirm family relationships or weed out sham marriages. Employers sometimes decide whether to hire people based on their online profiles, with one study indicating that 70 percent of recruiters and human resource professionals in the United States have rejected candidates based on data found online. A company called Spokeo gathers online data for employers, the public and anyone else who wants it. The company even posts ads urging “HR Recruiters — Click Here Now!” and asking women to submit their boyfriends’ e-mail addresses for an analysis of their online photos and activities to learn “Is He Cheating on You?”
Stereotyping is alive and well in data aggregation. Your application for credit could be declined not on the basis of your own finances or credit history, but on the basis of aggregate data — what other people whose likes and dislikes are similar to yours have done. If guitar players or divorcing couples are more likely to renege on their credit-card bills, then the fact that you’ve looked at guitar ads or sent an e-mail to a divorce lawyer might cause a data aggregator to classify you as less credit-worthy. When an Atlanta man returned from his honeymoon, he found that his credit limit had been lowered to $3,800 from $10,800. The switch was not based on anything he had done but on aggregate data. A letter from the company told him, “Other customers who have used their card at establishments where you recently shopped have a poor repayment history with American Express.” (…)
In 2007 and 2008, the online advertising company NebuAd contracted with six Internet service providers to install hardware on their networks that monitored users’ Internet activities and transmitted that data to NebuAd’s servers for analysis and use in marketing. For an average of six months, NebuAd copied every e-mail, Web search or purchase that some 400,000 people sent over the Internet.
{ NY Times | Continue reading }
economics, marketing, spy & security, technology | February 6th, 2012 3:51 pm