pipeline
‘Do not go where the path may lead, go instead where there is no path and leave a trail.’ –Ralph Waldo Emerson
We sat around night after night getting stoned and trying to come up with original ideas to make money. Since Bo was broke, we decided that we would do two banks, one after the other, and use the distraction of the first to reduce the police presence at the second. We also wanted a natural barrier between the banks, some type of separation that would slow down the response from the first bank to the second. The simplest would be mountains or a river, something natural. (…)
Finally, we decided on our first bank, which was staffed by women. It was about two-and-a-half miles from the big bridge. It was sort of on the edge of a residential area. There was an easy exit to the main street and an adjacent residential street where we could change cars or follow the street all the way back to the bridge on-ramp by staying off the main avenue. For some reason, cops always want to go to the bank after it’s been robbed. They know you won’t be there, but they still go.
Better eat the green one? OK.
Almost every country in the EU last week approved the use of Meat Glue in food. Technically called thrombian, or transglutaminase (TG), it is an enzyme that food processors use to hold different kinds of meat together.
Imitation crab meat is one of the more common applications: it’s made from surimi, a “fish-based food product” made by pulverizing white fish like pollock or hake into a paste, which is then mixed with meat glue so that the shreds stick together and hold the shape wanted for it by its creator.
Chicken nuggets are also often bound with meat glue, as are meat mixtures meant to mold like sausage but without the casing. Meat glue is also used by high-end chefs like New York restaurant WD-50’s Wylie Dufresne, who is famous for his shrimp pasta dish—instead of shrimp with pasta, he just makes the pasta out of shrimp.
What’s in a name? That which we call a rose.
In a notification sent to all service providers and hosting companies in Turkey on Thursday (28 April), the Telecommunication Communication Presidency (TİB) forwarded a list of banned words and terms. (…)
[Some of the banned words:] Adrianne, Animal, Sister-in-law, Blond, Beat, Enlarger, Nude, Crispy, Escort, Skirt, Fire, Girl, Free, Gay, Homemade, Liseli (’high school student’).
Just because you’re paranoid doesn’t mean they’re not after you
Criminology has yet to achieve full recognition as an independent discipline. (…)
When criminology began to make claims as an independent discipline, it came under heavy attack and the knowledge it produces was criticized as a producer of and product of power–knowledge. (…)
As a case in point, political violence and armed conflict have traditionally been neglected by criminologists, as some consider them to lie outside the realm of the discipline. Criminology has shied away from the study of atrocities, genocide, human rights violations, crimes against humanity, and war crimes, particularly from a perspective that centres on imbalances of social power within societies. However, since the late 1990s and particularly since the beginning of the new millennium, criminologists have been looking beyond terrorism and have started to investigate a multiplicity of topics, such as genocide, torture, child soldiers, war, crimes against humanity, and so on.
There are the gates of the roads of Night and Day
Meet Donald Trump’s bankers. Like the characters in the fairy tale The Emperor’s New Clothes, a gaggle of major financial institutions has finally been forced to admit, after lending Trump billions of dollars, that there’s a lot less to the emperor — or at least his empire — than the banks had believed.
Not quite nine months after bailing out Trump with a rescue package that gave him $65 million in new loans and eased credit terms on his bank debt, Trump’s bankers last week stopped the game. Already more than $3.8 billion in the hole and sliding perilously close to a mammoth personal bankruptcy, the brash New York developer had no choice but to accept the dismantling of his vast holdings.
related { Trump Unable To Produce Certificate Proving He’s Not A Festering Pile Of Shit }
unrelated { Why is the Federal Reserve forking over $220 million in bailout money to the wives of two Morgan Stanley bigwigs? }
To wait to date and the jake

For almost two years, Alex Pentland at the Massachusetts Institute of Technology has tracked 60 families living in campus quarters via sensors and software on their smartphones—recording their movements, relationships, moods, health, calling habits and spending. In this wealth of intimate detail, he is finding patterns of human behavior that could reveal how millions of people interact at home, work and play.
Through these and other cellphone research projects, scientists are able to pinpoint “influencers,” the people most likely to make others change their minds. The data can predict with uncanny accuracy where people are likely to be at any given time in the future. Cellphone companies are already using these techniques to predict—based on a customer’s social circle of friends—which people are most likely to defect to other carriers.
photo { Sarah Small }
From eighty six to ninety six the game went from sugar to shit

What is protected in the fashion world via the law and legislation, and what is not? Blakely: The main protection fashion designers have is over their trademark: their logo, their name. Source is protected; that’s why you hear about raids on pirates, who have made copies of Louis Vuitton bags, Canal St. in New York (NYC), Santee Alley in Los Angeles (LA). Have control of their name; have copyright protection of all the two-dimensional designs that go into the production of a garment. Textile design with a certain pattern–automatically qualify for copyright protection of that design. What they don’t own are any of the three-dimensional designs they end up creating. The stuff you see prancing out on a runway are actually up for grabs. Anybody can copy any aspects of any of those designs and get into no trouble with the law. Those designs are not particularly utilitarian–a word that comes up a lot in this industry–utilitarian stuff tends not to be protected legally. Something has to be considered a work of art in order to be considered for copyright protection. The courts decided long ago that they did not want any fashion designers owning such utilitarian designs as shirts, blouses, pants, belts, lapels. Don’t want somebody owning a monopoly–basically what a copyright gives you. (…)
Standard view would be: If I think my design is going to be copied, and copied quickly–which is what has happened to some extent because the copying ability better and the speed faster–then you’d think people would have less incentive to create new and better designs. That does not seem to be the case in the fashion industry. Why? Several reasons. One, from the beginning, copyright has both given artists an advantage and also taken something away. What it takes away from creators is access to other creative designs. Copyright holders may own what they have, but they cannot sample freely from others around them. Huge problem in the film and music industry. The fashion industry doesn’t suffer from this problem because every design that has ever been made is within a type of public domain. It is the raw material they can sample from to make their new work. Rich archive. The history of fashion, every hem length, every curved seam, every style is available to sample from. Not just stealing–sort of a curatorial responsibility. They are curating. Different gestures, different design elements from the past. Inevitably creating something new.
{ Johanna Blakley on Fashion and Intellectual Property | EconTalk | Continue reading }
photo { Bianca Jagger by Andy Warhol }
If I didn’t smell so good would you still hug me?
If you think global warming is some distant threat, come visit Yellowstone, our most beloved national park. Acres of trees are dying, trout runs are disappearing, and starving bears are attacking campers. It’s an ecosystem in collapse, and things are only getting worse.
{ Men’s Journal | Continue reading }
After world crude oil prices collapsed in 1985 (temporarily below $5 per barrel), American SUVs began their rapid diffusion that culminated in using the Hummer H1, a civilian version of a U.S. military assault vehicle weighing nearly 3.5 tonnes, for trips to grocery stores.
As the bouncer is a Sumo wrestler cream-puff casper milktoast
In the community of believers, paranormal sexual encounters are known as “spectrophilia.” Whether it’s invisible kisses and caresses, sex with Satan, phantom fornication, or obscene phone calls from the dead, let’s explore some claims of anomalous amorous phenomena.
I feel you would need one more for Hamlet. Seven is dear to the mystic mind. The shining seven W. B. calls them.
JamesMTitus was manufactured by cyber-security specialists in New Zealand participating in a two-week social-engineering experiment organized by the Web Ecology Project. Based in Boston, the group had conducted demographic analyses of Chatroulette and studies of Twitter networks during the recent Middle East protests. It was now interested in a question of particular concern to social-media experts and marketers: Is it possible not only to infiltrate social networks, but also to influence them on a large scale?
The group invited three teams to program “social bots”—fake identities—that could mimic human conversation on Twitter, and then picked 500 real users on the social network, the core of whom shared a fondness for cats. The Kiwis armed JamesMTitus with a database of generic responses (“Oh, that’s very interesting, tell me more about that”) and designed it to systematically test parts of the network for what tweets generated the most responses, and then to talk to the most responsive people.
After the first week, the teams were allowed to tweak their bot’s code and to launch secondary identities designed to sabotage their competitors’ bots.
Justice is what the judge ate for breakfast
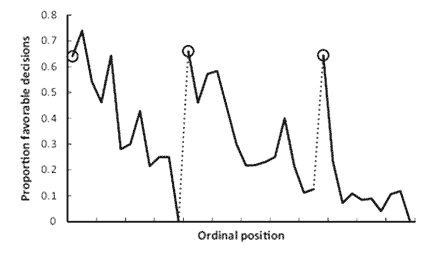
{ How food-breaks sway the decisions of judges. The graph above shows that the odds that prisoners will be successfully paroled start off fairly high at around 65% and quickly plummet to nothing over a few hours (although, see footnote). After the judges have returned from their breaks, the odds abruptly climb back up to 65%, before resuming their downward slide. | Discover | full story }
It was easy. I told them I was you, I acted real stupid and they believed me.
Forget passwords, tricky sums are more secure
Classic user identification requires the remote user sending a username and a password to the system to which they want to be authenticated. The system looks up the username in its locally stored database and if the password submitted matches the stored password, then access is granted. This method for identification works under the assumption there exist no malicious users and that their local terminals cannot be infected by malware. (…)
Nikolaos Bardis of the University of Military Education, in Vari, Greece and colleagues there and at the Polytechnic Institute of Kiev, in Ukraine, have developed an innovative approach to logins, which implements the advanced concept of zero knowledge identification.
Zero knowledge user identification solves these issues by using passwords that change for every session and are not known to the system beforehand. The system can only check their validity.
In bed with a couple of eggs since the City arms hotel

Remember Paul Ceglia? He’s the fellow in upstate New York who sued Mark Zuckerberg last July, claiming that, way back in 2003, Zuckerberg had agreed to give him a 50% ownership in the project that became Facebook.
That claim seemed preposterous at the time, not least because Ceglia had waited 7 years to file it. And there was also the fact that Ceglia was a convicted felon, having been charged with criminal fraud in connection with a wood-pellet company he operated. (…)
But now Paul Ceglia has refiled his lawsuit. With a much larger law firm. And a lot more evidence. And the new evidence is startling.
And her name is Ursula

The process of development is an astounding journey from simplicity to complexity. You start with a single cell, the fertilized egg, and you end up with a complete multicellular organism, made up of tissues that self-organize from many individual cells of different types. The question of how cells know who to be and where to go has many layers to it, starting with the question of how you lay down the basic body plan (head here, tail there, which side is left and where does the heart go?) and continuing on down to microscopic structures, with questions such as how and where to form the small tubes that will allow blood to permeate through apparently solid tissues. This kind of self-organizing behavior is deeply interesting to robotics researchers (who would love to copy it) and tissue engineers (who would like to manipulate it).
A recent paper (Parsa et al. 2011. Uncovering the behaviors of individual cells within a multicellular microvascular community) takes a close look at self-organization on the micro level. (…)
Despite the tremendous variability in the paths followed by individual cells, the authors hoped to find patterns in their data that might provide insight into how the network forms. And luckily, the patterns were there to find. Using a clustering algorithm, they identified groups of cells that behaved similarly to each other with respect to specific sets of behavioral parameters. For example, looking at the pattern of how the area of a cell grows and shrinks allowed the authors to define three major clusters of cells that accounted for about 2/3 of the cells in their study. In the same way, they could define subsets of cells that moved through the gel in similar ways. Although these clusters are rather broadly defined, they seem to be telling us something important about differences between the cells in the different subsets; the subset of cells that spread early (with areas showing a peak at 60 or 120 minutes) are more likely to end up as connection points in the network, while the cells that spread late (300 minutes) tend to end up as branches between the connection points.
photo { Charlie Engman }
Snuffed out the ghost in the candle at his old game of haunt

In a closely-watched oral argument Monday at a federal courthouse in Washington, the core questions of the case read like scripts from a college philosophy exam: are isolated human genes and the subsequent comparisons of their sequences patentable? Can one company own a monopoly on such genes without violating the rights of others? They are multi-billion dollar questions, the judicially-sanctioned answers to which will have enormous ramifications for the worlds of medicine, science, law, business, politics and religion.
Even the name of the case at the U.S. Circuit Court for the Federal Circuit — Association of Molecular Pathology, et al. v United States Patent and Trademark Office, et al — oozes significance. The appeals court judges have been asked to determine whether seven existing patents covering two genes — BRCA1 and BRCA2 (a/k/a “Breast Cancer Susceptibility Genes 1 and 2″) — are valid under federal law or, instead, fall under statutory exceptions that preclude from patentability what the law identifies as ”products of nature.”
In other words, no one can patent a human being. Not yet anyway.
painting { Jenny Saville, Plan, 1993 }
With kisses drunk, you drop your heads in the sublimely sobering water

{ Fukushima Fallout Reaches San Francisco. Small amounts of radioactive material have turned up in rainwater in the Bay Area, say nuclear scientists. | The Physics arXiv Blog | full story | Read more: The Bulletin of the Atomic Scientists | Fukushima in focus: collection of coverage }
artwork { Ruel Pascual }
Ice & Arrows

In the 2006 movie, Borat: Cutural Learnings of America for Make Benefit Glorious Nation of Kazakhstan, English comedian Sacha Baron Cohen plays the role of an outrageously inappropriate Kazakh television reporter who journeys across the United States to film a documentary about American culture. In the course of his travels, the title character uses his bizarre persona to elicit offensive statements and behavior from, as well as to generally humiliate, a number of ordinary Americans who are clearly not in on the joke. How did the producers convince these unfortunate stooges to participate in the project? According to several who later sued, the producers lied about the identity of Borat and the nature of the movie when setting up the encounters in advance over the telephone, and they then contradicted and disclaimed the lies in a waiver that the stooges signed without reading just before the cameras began to roll.
This talk article explains the doctrinal and normative reasons that the Borat problem, which arises frequently, although usually in more mundane contexts, divides courts. It then suggests an approach for courts to use when facing the problem that minimizes risks of exploitation and costs of contracting.
{ The ‘Borat’ Problem and the Law of Negotiation | Continue reading }
photo { Alpines, the Night Drive EP, 500 individually numbered 10″ Vinyl Discs }