technology

{ The patterns of links between buyers and sellers of sex in an online forum differs in important ways from other internet related networks, says a new study. This may have important implications for the spread of sexually transmitted diseases | Patterns of Captured in Social Network | full story }
update/related { A top journalist caught on tape with a pile of cocaine and a party girl named Moomoo, an opposition activist filmed handing over a bribe… Who’s behind the spate of mysterious coke-and-hooker entrapment attacks on Russian opposition figures? The Daily Beast | full story }
economics, health, science, sex-oriented, social networks | March 23rd, 2010 2:00 pm
relationships, social networks | March 23rd, 2010 12:57 pm
future, music, technology | March 23rd, 2010 12:32 pm

…sooner or later, helium will become more precious than gold. Though best known as the lifting gas in balloons (and the high squeaky voices it evokes when inhaled), helium’s buoyancy, inertness, and other unique properties make it irreplaceable for some of our civilization’s highest technologies. Without large amounts of helium, liquid-fueled rockets cannot be safely tested and launched, semiconductors and optical fibers cannot be easily manufactured, and cryogenically cooled particle accelerators and medical MRI machines cannot function. Helium may also prove crucial as a working fluid or even a fuel in future nuclear reactors. And unlike gold, which can be eternally recovered and shaped to new functions, only very expensive countermeasures can prevent helium, once used, from escaping into the atmosphere and drifting away into outer space.
Helium’s rarity on Earth and relative abundance in America are cosmic and planetary accidents. After hydrogen, helium is the second most common element in the universe, with the bulk of it formed during the big bang.
{ Seed magazine | Continue reading }
photo { Stephen Shore }
elements, science, technology | March 18th, 2010 2:45 pm

“Perhaps most troubling,” says the report, “the FBI could not determine in many cases whether the lost or stolen laptop computers contained sensitive or classified information. Such information may include case information, personal identifying information, or classified information on FBI operations.” Laptops can also contain goodies like the software that the FBI uses to make its identification badges, a copy of which was installed on a laptop stolen from the Boston Field Office in July 2002.
In the 44 months that it took to complete the new audit, the FBI lost 160 weapons and 160 laptop computers—a massive improvement over the 354 weapons and 317 laptops lost during the first 28-month-long audit. In any organization the size of the FBI, equipment is going to be lost, misplaced, or stolen, so perfection is not to be expected.
{ Ars Technica, 2007 | Continue reading }
U.S., incidents, technology, uh oh | March 17th, 2010 8:12 pm
{ New Charging Method Could Slash Battery Recharge Times | The Physics arXiv Blog | full story }
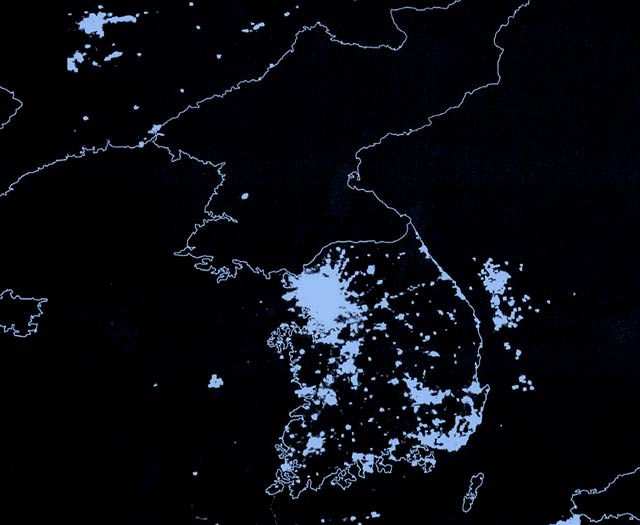
photo { A Department of Defense satellite image of the Korean Peninsula showing wide illuminated areas in South Korea and the relative darkness of the North, September 2003 | Jason Reed/Reuters }
asia, technology | March 11th, 2010 4:47 pm
economics, technology | March 11th, 2010 4:46 pm

Building a nuclear weapon has never been easier. NATO’s Michael Rühle provides step-by-step instructions for going nuclear, from discretely collecting material to minimizing the fallout when caught. These simple steps have worked for the likes of Israel, Pakistan, and North Korea, among others. The nuclear club is open to your country, too.
{ IP Global | Continue reading }
horror, incidents, technology | March 11th, 2010 4:46 pm

Scientists have spent the past decade making great strides in the field of brain-computer interfaces (BCI). By attaching a series of electrodes to a human brain, researchers can feed neural impulses from the brain into a computer to allow the direct control of robotic devices. One major downside, of course, is that the electrodes through which the subject controls these robotic devices have to be placed directly on the brain. This drawback had been in large part considered unavoidable, as electrodes placed outside the skull were thought to gather insufficient information to successfully operate a mechanical device. But in a study published last week in The Journal of Neuroscience, researchers were able to use an array of 34 electrodes attached to test-subjects’ scalps to deduce the subjects’ 3-dimensional hand movements. The importance of this work is clear: It may help patients who have lost a limb to operate a replacement robotic prostheses with their brain.
{ Seed | Continue reading }
related { Brain-Computer Interface Live demonstration of a brain-controlled Adams Family pinball machine | video }
brain, technology | March 11th, 2010 4:46 pm

Let’s define the term “value” as “a fair equivalent in money for something sold.”
Let’s define “devalue” as “to lessen the worth off something sold.”
So does a $1.99 price point for ebooks constitute their value? Or does that price devalue the work?
In a capitalist economy, under the rules of supply and demand, things cost money to produce, and their price is dictated by how many things are produced and how many people want to buy them.
An item usually costs a determined amount to create (which tends to go down as more items are produced), and then wholesalers and retailers sell this item for what the market will bear, trying to make a profit.
A few years ago, when the Nintendo Wii was a hot item and hard to find, people who were able to get Wiis sold them on eBay for more than double the $199 list price. The Wii’s value was higher, because demand was higher.
Now you can buy used Wii’s for less than $100. There is a big enough supply for everyone, so the price comes down.
So how do ebooks fit into this?
For the moment, let’s ignore the hard work the author has put into writing the book.
To bring an ebook to market, a book needs to be edited, proofread, put into a proper layout and format, and given cover art and a product description.
These costs can fluctuate. But they are one-time costs.
Once an ebook is created, it can be reproduced indefinitely for free. There are no printing costs or shipping costs. Distributing ebooks to readers costs about 5 cents per download.
{ Joe Konrath | Continue reading }
books, economics, technology | March 11th, 2010 4:45 pm

In the emerging world of e-books, many consumers assume it is only logical that publishers are saving vast amounts by not having to print or distribute paper books, leaving room to pass along those savings to their customers.
Publishers largely agree, which is why in negotiations with Apple, five of the six largest publishers of trade books have said they would price most digital editions of new fiction and nonfiction books from $12.99 to $14.99 on the forthcoming iPad tablet — significantly lower than the average $26 price for a hardcover book.
But publishers also say consumers exaggerate the savings and have developed unrealistic expectations about how low the prices of e-books can go. Yes, they say, printing costs may vanish, but a raft of expenses that apply to all books, like overhead, marketing and royalties, are still in effect.
{ NY Times | Continue reading }
quote { Morgan Meis, Photography’s surprising impact on the Surrealists }
related { To keep pace in this climate of innovation, we are proud to announce our groundbreaking new 3-D print edition. }
books, economics, technology | March 9th, 2010 4:18 am

Information theory is a branch of applied mathematics and electrical engineering involving the quantification of information. (…)
A key measure of information in the theory is known as entropy, which is usually expressed by the average number of bits needed for storage or communication. Intuitively, entropy quantifies the uncertainty involved when encountering a random variable. For example, a fair coin flip (2 equally likely outcomes) will have less entropy than a roll of a die (6 equally likely outcomes).
{ Wikipedia | Continue reading }
Claude Elwood Shannon (1916 – 2001), an American electronic engineer and mathematician, is known as “the father of information theory.”
Shannon is famous for having founded information theory with one landmark paper published in 1948. But he is also credited with founding both digital computer and digital circuit design theory in 1937, when, as a 21-year-old master’s student at MIT, he wrote a thesis demonstrating that electrical application of Boolean algebra could construct and resolve any logical, numerical relationship. It has been claimed that this was the most important master’s thesis of all time. (…)
The Las Vegas connection: Information theory and its applications to game theory
Shannon and his wife Betty also used to go on weekends to Las Vegas with M.I.T. mathematician Ed Thorp, and made very successful forays in blackjack using game theory type methods co-developed with physicist John L. Kelly Jr. based on principles of information theory. They made a fortune, as detailed in the book Fortune’s Formula. (…)
Shannon and Thorp also applied the same theory, later known as the Kelly criterion, to the stock market with even better results.
{ Wikipedia | Continue reading | Mathematical Theory of Claude Shannon, A study of the style and context of his work up to the genesis of information theory. | PDF }
recto/verso { Welcome to Fabulous Las Vegas sign, 1959, designed by Betty Willis. | In hopes that the design would be used freely, Willis never copyrighted her sign’s design. | PBS | Continue reading | More Betty Willis | NY Times | Photos: The Neon Museum, Las Vegas }
mathematics, technology, theory, vegas | March 4th, 2010 6:23 pm

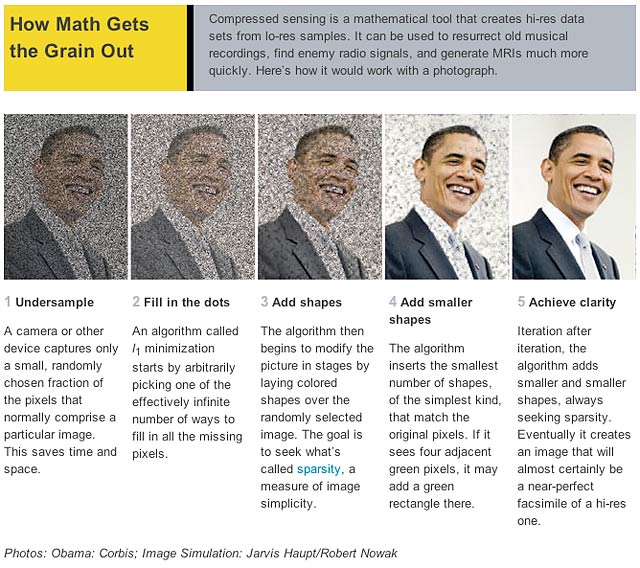
The mathematics that describe both sensory perception and the transmission of information turn out to have remarkable similarities.
In 1834, the German physiologist Ernst Weber carried out a series of experiments to determine the limits of sensory perception. He gave a blindfolded man a mass to hold and gradually increased its weight, asking the subject to indicate when he first became aware of the change.
These experiments showed that the smallest increase in weight that a human can perceive is proportional to the initial weight. The German psychologist Gustav Fechner later interpreted Weber’s work as a way of measuring the relationship between the physical magnitude of a stimulus and its perceived intensity.
The resultant mathematical model of this process is called the Weber-Fechner law and shows that the relationship between the stimulus and perception is logarithmic. The Weber-Fechner law is important because it established a new field of study called psychophysics. (…)
The logarithmic relationship between a stimulus and its perception crops up in various well known examples such as the logarithmic decibel scale for measuring sound intensity and a similar logarithmic scale for measuring the visible brightness of stars, their magnitude.
Today, Hi Jun Choe, a mathematician at Yonsei University in South Korea, says there is an interesting connection between the Weber-Fechner Law and the famous mathematical theory of information developed by Claude Shannon at Bell Labs in the 1940s.
Shannon’s work is among the most important of the 20th century. It establishes the limits on the amount of information that can be sent from one location in the universe to another. It is no exaggeration to say that the world’s entire computing and communications infrastructure is based on Shannon’s work. (…)
Of course, the idea that sensory perception is a form of communication and so obeys the same rules, is not entirely surprising. What’s astonishing (if true) is that the connection has never been noticed before.
{ The Physics arXiv Blog | Continue reading }
mathematics, science, technology | March 4th, 2010 6:22 pm

Mirage: The Omnidroid 9000 is a top-secret military fighting robot. Artificial intelligence allows it to solve any problem it’s presented with, and, unfortunately…
Mr. Incredible: Let me guess. It became smart enough to wonder why it had to take orders.
Mirage: We lost control, and now it’s loose in the jungle, threatening our facility.
{ The Incredibles, 2004 }
Dave: Open the pod bay doors, HAL.
HAL: I’m sorry, Dave. I’m afraid I can’t do that.
Dave: What’s the problem?
HAL: I think you know what the problem is just as well as I do.
Dave: I don’t know what you’re talking about, HAL.
HAL: I know that you and Frank were planning to disconnect me, and I’m afraid that’s something I cannot allow to happen.
{ 2001: A Space Odyssey, 1968 }
future, haha, incidents, robots & ai, showbiz, space | March 4th, 2010 6:20 pm

In recent years Britain has become the Willy Wonka of social control, churning out increasingly creepy, bizarre, and fantastic methods for policing the populace. But our weaponization of classical music—where Mozart, Beethoven, and other greats have been turned into tools of state repression—marks a new low.
We’re already the kings of CCTV. An estimated 20 per cent of the world’s CCTV cameras are in the UK, a remarkable achievement for an island that occupies only 0.2 per cent of the world’s inhabitable landmass.
A few years ago some local authorities introduced the Mosquito, a gadget that emits a noise that sounds like a faint buzz to people over the age of 20 but which is so high-pitched, so piercing, and so unbearable to the delicate ear drums of anyone under 20 that they cannot remain in earshot. It’s designed to drive away unruly youth from public spaces, yet is so brutally indiscriminate that it also drives away good kids, terrifies toddlers, and wakes sleeping babes.
Police in the West of England recently started using super-bright halogen lights to temporarily blind misbehaving youngsters. From helicopters, the cops beam the spotlights at youths drinking or loitering in parks, in the hope that they will become so bamboozled that (when they recover their eyesight) they will stagger home. (…)
In January it was revealed that West Park School, in Derby in the midlands of England, was “subjecting” (its words) badly behaved children to Mozart and others. In “special detentions,” the children are forced to endure two hours of classical music both as a relaxant (the headmaster claims it calms them down) and as a deterrent against future bad behavior.
{ Reason | Continue reading }
artwork { Stuart Patterson }
music, noise and signals, pipeline, technology, uh oh | March 4th, 2010 6:15 pm

The general problem of data preservation is twofold. The first matter is preservation of the data itself: The physical media on which data are written must be preserved, and this media must continue to accurately hold the data that are entrusted to it. This problem is the same for analog and digital media, but unless we are careful, digital media can be more fragile.
The second part of the equation is the comprehensibility of the data. Even if the storage medium survives perfectly, it will be of no use unless we can read and understand the data on it. With most analog technologies such as photographic prints and paper text documents, one can look directly at the medium to access the information. With all digital media, a machine and software are required to read and translate the data into a human-observable and comprehensible form. If the machine or software is lost, the data are likely to be unavailable or, effectively, lost as well.
Unlike the many venerable institutions that have for centuries refined their techniques for preserving analog data on clay, stone, ceramic or paper, we have no corresponding reservoir of historical wisdom to teach us how to save our digital data. That does not mean there is nothing to learn from the past, only that we must work a little harder to find it.
{ American Scientist | Continue reading }
future, technology | March 4th, 2010 6:11 pm

Two years ago, when the FBI was stymied by a band of armed robbers known as the “Scarecrow Bandits” that had robbed more than 20 Texas banks, it came up with a novel method of locating the thieves.
FBI agents obtained logs from mobile phone companies corresponding to what their cellular towers had recorded at the time of a dozen different bank robberies in the Dallas area. The voluminous records showed that two phones had made calls around the time of all 12 heists, and that those phones belonged to men named Tony Hewitt and Corey Duffey. A jury eventually convicted the duo of multiple bank robbery and weapons charges.
Even though police are tapping into the locations of mobile phones thousands of times a year, the legal ground rules remain unclear, and federal privacy laws written a generation ago are ambiguous at best. On Friday, the first federal appeals court to consider the topic will hear oral arguments (PDF) in a case that could establish new standards for locating wireless devices.
{ CNET | Continue reading }
spy & security, technology | March 4th, 2010 6:08 pm

Mattel recently conducted an online poll asking girls everywhere to choose Barbie’s next occupation from the following choices — surgeon, architect, news anchor, environmentalist and computer engineer.
The overwhelming choice among the girls was news anchor. But adults in the blogosphere, on Twitter and Facebook launched their own campaign for computer engineer Barbie. Mattel relented and decided to go with both, news anchor and computer engineer Barbie.
The Barbie brouhaha points to a key conundrum today when it comes to women and professions in science and technology. Many people see a need for more females in so-called STEM professions (science, technology, engineering and math). But fewer and fewer young women seem to be gravitating to such jobs.
{ MSNBC | Continue reading }
economics, technology | March 4th, 2010 6:06 pm

1 out of every 10 electrons you consume in America comes from dismantled Russian warheads. Half the uranium we consume comes from a program called Megatons to Megawatts. And 20% of our electricity comes from nuclear. Hence 10% of all electricity in this country comes from post-Cold War weapons dismantling. Bombs once pointed at your cities now power them—from swords to ploughshares, indeed.
{ Josh Wolfe Newsletter, Feb 19, 2010 }
U.S., economics, technology | February 25th, 2010 8:50 pm