
Google Brain has created two artificial intelligences that evolved their own cryptographic algorithm to protect their messages from a third AI, which was trying to evolve its own method to crack the AI-generated crypto. The study was a success: the first two AIs learnt how to communicate securely from scratch.
{ Ars Technica | Continue reading }
images { American Apparel ad, Vice magazine, 2008 | Richard Prince, Untitled, 2012-14 }
unrelated { This Year, You Can Wear A ‘Vagina Mask’ For Halloween | Thanks Tim }
halves-pairs, technology |
October 28th, 2016

If you were at work last Friday, you might have noticed that you couldn’t get on Twitter, Spotify, [Amazon, Tumblr, Reddit, Netflix…]. The sites themselves were fine, but users across the country lost access due to a large-scale attack on Dyn, a company whose servers provide infrastructure and routing services for the internet’s top destinations.
{ Bloomberg | Continue reading }
Allison Nixon, director of research at Flashpoint, said the botnet used in today’s ongoing attack is built on the backs of hacked IoT devices — mainly compromised digital video recorders (DVRs) and IP cameras made by a Chinese hi-tech company called XiongMai Technologies. The components that XiongMai makes are sold downstream to vendors who then use it in their own products.
“It’s remarkable that virtually an entire company’s product line has just been turned into a botnet that is now attacking the United States,” Nixon said.
{ Brian Krebs | Continue reading }
related { Chinese Firm Behind Friday’s Internet Outage Threatens Western Accusers With Lawsuits }
related { Last month the Exploratorium was the target of a cyberattack. This is an account of what we think happened and how we dealt with it. }
technology |
October 24th, 2016
We fail to see that a computer that is a hundred times more accurate than a human, and a million times faster, will make 10,000 times as many mistakes.
{ The Guardian | Continue reading }
related { Robots Will Replace Doctors, Lawyers, and Other Professionals }
art { electropollock | video }
technology, uh oh |
October 11th, 2016
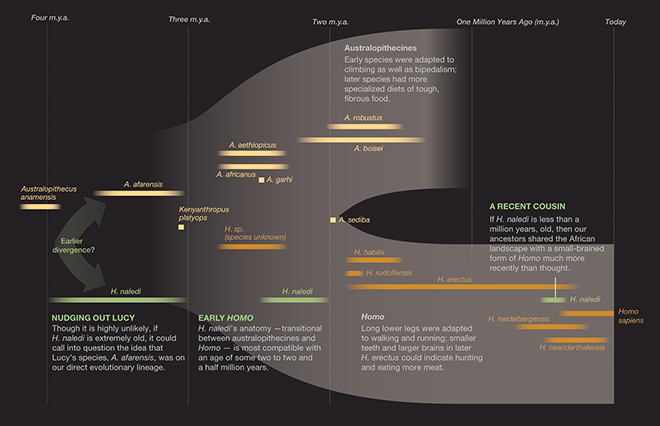
Our human family tree used to be a scraggly thing. With relatively few fossils to work from, scientists’ best guess was that they could all be assigned to just two lineages, one of which went extinct and the other of which ultimately gave rise to us. Discoveries made over the past few decades have revealed a far more luxuriant tree, however — one abounding with branches and twigs that eventually petered out. In fact, a new species, called Homo naledi, as yet undated, was announced just last year. This newfound diversity paints a much more interesting picture of our origins but makes sorting our ancestors from the evolutionary dead ends all the more challenging.
{ Scientific American | Continue reading | More: National Geographics }
flashback |
October 11th, 2016

Why so many of America’s sushi restaurants are Chinese-owned
The influx of low-wage Chinese immigrants — China recently eclipsed Mexico as the largest source of immigrants to the United States — has created fierce competition to provide cheap food. At the same time, Japan’s wealth and economic success helped its cuisine gain a reputation as trendy and refined. So for many entrepreneurial Chinese immigrants looking to get ahead, Japanese food has often become the better opportunity.
“Chinese entrepreneurs have figured out that this is a way to make a slightly better living and get out of the . . . world of $10, $5 food at the bottom end of the market,” says Krishnendu Ray, who leads New York University’s food studies program. […]
“Japanese food has more prestige and seems to, if you just look at a menu, have greater economic opportunity attached to it, because people are conditioned to pay more for rice and protein when it’s presented as sushi than rice and protein when it’s presented as a stir fry,” said Sasha Issenberg, author of “The Sushi Economy.” […]
“I can tell you it is easier to do than a Chinese restaurant,” says Kin Lee, the owner of Love Sushi in Gaithersburg, Md., “and the profit margins are better.”
{ Washington Post | Continue reading }
economics, food, drinks, restaurants |
October 5th, 2016
Recently, experimental psychologists at Oxford University explored the function of kissing in romantic relationships.
Surprise! It’s complicated.
After conducting an online survey with 308 men and 594 women, mostly from North America and Europe, who ranged in age from 18 to 63, the researchers have concluded that kissing may help people assess potential mates and then maintain those relationships.
“The repurposing of the behavior is very efficient,” said Rafael Wlodarski, a doctoral candidate and lead author of the study, published in Archives of Sexual Behavior.
But another hypothesis about kissing — that its function is to elevate sexual arousal and ready a couple for coitus — didn’t hold up. While that might be an outcome, researchers did not find sexual arousal to be the primary driver for kissing. […]
The participants generally rated kissing in casual relationships as most important before sex, less important during sex, even less important after sex and least important “at other times.” (To clarify: researchers defined kissing as “on the lips or open-mouth (French).”)
{ NY Times | Continue reading }
relationships |
September 26th, 2016

When used in speech, hesitancies can indicate a pause for thought, when read in a transcript they indicate uncertainty. In a series of experiments the perceived uncertainty of the transcript was shown to be higher than the perceived uncertainty of the spoken version with almost no overlap for any respondent.
{ arXiv | Continue reading }
art { Paul Klee, After the drawing 19/75, 1919 }
ideas |
September 20th, 2016
In early 2015, near the end of my MFA in Fine Arts at Parsons, I set out on a project to create a celebrity by 2020—entirely via the internet—as an art practice. The celebrity I began to create was a hyper sexy, cyber savvy, female rock star named Ona.
Without a large budget or industry connections, I knew that major social media growth would be an important factor. I started by employing some of the usual tactics I’d used in the past for other projects—a press release, an article in Thought Catalog, soliciting articles from journalists. Nothing much came of it.
So I tried a different tack, working with what I already had: two Instagram accounts, each with a couple hundred followers—one for my art practice as a whole (@leahschrager) and one specifically for selfies and modeling (@onaartist). It was immediately clear that the selfies I posted on @onaartist got more likes and the account grew more quickly. I sought out modeling accounts with big follower numbers and I started DMing them, asking the models if I could pay them to talk to me about how they grew. None of them got back to me. I then did some open submissions to @playboy, @arsenicmagazine, and a few others, but I didn’t get picked.
Finally, I DMed a collection page—a page with a large follower count that features photos of various models—and it got back to me. The page was @the.buttblog, and I was told it would cost $200 for a permanent post. I paid its admin to post a photo of me and in 24 hours I gained around 5,000 real followers.
{ Leah Schrager/Rhizome | Continue reading }
marker on inkjet print { Leah Schrager }
experience |
September 20th, 2016

In 2012, hedge fund manager and venture capitalist Albert Hu was convicted of a financial fraud that stretched from Silicon Valley to Hong Kong. Today, he is locked up in the minimum security wing of Lompoc federal prison—inmate #131600-111—without access to the Internet. But, somehow, his bogus investment firm has come back to life.
On the surface, Asenqua Ventures appears to be legitimate. It has a website. It has a working voicemail system and lists a Northern California office address. It has distributed multiple press releases via PRNewswire, which were then picked up by reputable media organizations. It is included in financial industry databases like Crunchbase, PitchBook, and S&P Capital IQ. Its senior managers have LinkedIn profiles.
One of those profiles belonged to Stephen Adler, who earlier this week sent out hundreds of new Linkedin “connect” invitations (many of which were accepted). Among the recipients was Marty McMahon, a veteran executive recruiter who just felt that something was a bit off about Adler’s profile. So he did a Google reverse image search on Adler’s profile pic, and quickly learned that the headshot actually belonged to a San Diego real estate agent named Dan Becker.
McMahon called Dan Becker, who he says was stunned to learn that his photo was being used by someone who he didn’t know. Then McMahon did another image search for the LinkedIn profile pic of Adler’s colleague, Michael Reed. This time it led him to Will Fagan, another San Diego realtor who often works with Dan Becker.
{ Fortune | Continue reading }
economics, scams and heists |
September 19th, 2016

For hundreds of years, Koreans have used a different method to count age than most of the world. […] A person’s Korean age goes up a year on new year’s day, not on his or her birthday. So when a baby is born on Dec. 31, he or she actually turns two the very next day.
{ Quartz | Continue reading }
asia, time |
September 16th, 2016
sex-oriented |
September 15th, 2016
Someone Is Learning How to Take Down the Internet
Recently, some of the major companies that provide the basic infrastructure that makes the Internet work have seen an increase in DDoS attacks against them. Moreover, they have seen a certain profile of attacks. These attacks are significantly larger than the ones they’re used to seeing. They last longer. They’re more sophisticated. And they look like probing. One week, the attack would start at a particular level of attack and slowly ramp up before stopping. The next week, it would start at that higher point and continue. And so on, along those lines, as if the attacker were looking for the exact point of failure. […]
We don’t know where the attacks come from. The data I see suggests China, an assessment shared by the people I spoke with. On the other hand, it’s possible to disguise the country of origin for these sorts of attacks. The NSA, which has more surveillance in the Internet backbone than everyone else combined, probably has a better idea, but unless the US decides to make an international incident over this, we won’t see any attribution.
{ Bruce Schneier | Continue reading }
polaroid photograph { Andy Warhol, Grapes, 1981 }
spy & security, technology |
September 14th, 2016

Why Scientific Studies Are So Often Wrong: The Streetlight Effect
Researchers tend to look for answers where the looking is good, rather than where the answers are likely to be hiding.
{ Discover | Continue reading }
science |
September 12th, 2016

Revisiting Depression Contagion […] A Speed-Dating Study.
After four minutes of interaction with partners with high levels of depressive symptoms, participants did not experience increased negative affect; instead, they experienced reduced positive affect, which led to the rejection of these partners.
{ Clinical Psychological Science | Continue reading }
psychology, relationships |
September 12th, 2016






















