technology

Remember Paul Ceglia? He’s the fellow in upstate New York who sued Mark Zuckerberg last July, claiming that, way back in 2003, Zuckerberg had agreed to give him a 50% ownership in the project that became Facebook.
That claim seemed preposterous at the time, not least because Ceglia had waited 7 years to file it. And there was also the fact that Ceglia was a convicted felon, having been charged with criminal fraud in connection with a wood-pellet company he operated. (…)
But now Paul Ceglia has refiled his lawsuit. With a much larger law firm. And a lot more evidence. And the new evidence is startling.
{ Business Insider | Continue reading }
economics, law, social networks | April 12th, 2011 3:04 pm

How Your Username May Betray You
By creating a distinctive username—and reusing it on multiple websites—you may be giving online marketers and scammers a simple way to track you. Four researchers from the French National Institute of Computer Science (INRIA) studied over 10 million usernames—collected from public Google profiles, eBay accounts, and several other sources. They found that about half of the usernames used on one site could be linked to another online profile, potentially allowing marketers and scammers to build a more complex picture of the users.
{ Technology Review | Continue reading }
guide, technology | April 6th, 2011 6:05 pm

{ $1,700: The annual benefit the average American derives from personal computers. | WSJ | full story }
U.S., economics, technology | April 4th, 2011 3:04 pm

Magnetism remains the most developed way to store digital information. The giga and terabytes of computer hard drives as well as the magnetic stripes that still are used for credit cards or hotel room keys, all function with the help of magnetic fields. There, the direction of the magnetic fields, up or down, expresses the digital 0s and 1s that make up the computer bits and bytes.
As the amount of data we store on hard drives continues to increase, it is of course desirable that read and write speeds follow that trend. (…)
In a paper published in advance on the Nature website this week, Ilie Radu, Theo Rasing from Radboud University in Nijmegen and others have investigated the details of the optical switching proceeds for a particular class of magnets, antiferromagnets.
{ All that matters | Continue reading }
photo { James Bond’s Rolex activates a “Hyper intensified magnetic field” “powerful enough to even deflect the path of a bullet at long range in Live and Let Die, 1971 }
science, technology | March 30th, 2011 6:59 pm

Microsoft’s recent takedown of the world’s largest spam engine offered tantalizing new clues to the identity and earnings of the Rustock botmasters. The data shows that Rustock’s curators made millions by pimping rogue Internet pharmacies, but also highlights the challenges that investigators still face in tracking down those responsible for building and profiting from this complex crime machine.
Earlier this month, Microsoft crippled Rustock by convincing a court to let it seize dozens of Rustock control servers that were scattered among several U.S.-based hosting providers. Shortly after that takedown, I began following the money trail to learn who ultimately paid the botnet controllers’ hosts for their services.
According to interviews with investigators involved in the Rustock takedown, approximately one-third of the control servers were rented from U.S. hosting providers by one entity: A small business in Eastern Europe that specializes in reselling hosting services to shadowy individuals who frequent underground hacker forums.
{ Brian Krebs | Continue reading }
scams and heists, technology | March 29th, 2011 8:15 pm

Because electronic information seems invisible, we underestimate the resources it takes to keep it all alive. The data centers dotting the globe, colloquially known as “server farms,” are major power users with considerable carbon footprints. Such huge clusters of servers not only require power to run but must also be cooled. In the United States, it’s estimated that server farms, which house Internet, business and telecommunications systems and store the bulk of our data, consume close to 3 percent of our national power supply. Worldwide, they use more power annually than Sweden. (…)
We can try hitting delete more often.
{ NY Times | Continue reading }
photo { Michael Rubenstein }
technology | March 27th, 2011 5:02 pm

{ The cellphone has been more than a cellphone for years, but soon it could take on an entirely new role — standing in for all of the credit and debit cards crammed into wallets. There’s just one hitch: While the technology is already being installed in millions of phones — and is used overseas — wide adoption of the so-called mobile wallets is being slowed by a major behind-the-scenes battle among corporate giants. | NY Times | Continue reading }
economics, technology | March 23rd, 2011 6:15 pm

Our problem with public cell phone conversations has nothing to do with how cool he thinks he is, or even his stupid voice. It’s all in our heads.
Science has proven that hearing half a conversation, as you’re forced to do when close to a cell phone user, is inherently more distracting to the human brain. In one experiment, people were asked to try to concentrate on a task in total silence, and then while overhearing two people conversing with each other. They performed equally well both times. But when half a conversation was played, performances dropped dramatically.
{ 6 Things That Annoy You Every Day (Explained by Science) | Cracked | Continue reading }
psychology, technology | March 23rd, 2011 4:35 pm

{ The New York Times paywall is costing the newspaper $40-$50 million to design and construct, Bloomberg has reported. And it can be defeated through four lines of Javascript. | Nieman Journalism Lab | full story | image: New York Times Magazine cover by John Maeda }
related:
{ Through a special agreement with more than 800 newspapers worldwide, the Newseum displays these front pages each day on its website. }
economics, press, technology | March 22nd, 2011 7:35 pm
A federal judge rejected Google’s $125 million class-action settlement with authors and publishers, delivering a blow to the company’s ambitious plan to build the world’s largest digital library and bookstore. (…)
The court’s decision throws into legal limbo one of Google’s most ambitious projects: a plan to digitize millions of books from libraries.
The Authors Guild and the Association of American Publishers sued Google in 2005 over its digitizing plans. After two years of painstaking negotiations, the authors and publishers devised with Google a sweeping settlement that would have helped to bring much of the publishing industry into the digital age.
The deal turned Google, the authors and the publishers into allies who defended the deal against an increasingly vocal chorus of opponents that included academics, copyright experts, the Justice Department and foreign governments. (…)
The deal would have allowed Google to make millions of out-of-print books broadly available online and to sell access to them, while giving authors and publishers new ways to earn money from digital copies of their works. Yet the deal faced a tidal wave of opposition from Google rivals like Amazon and Microsoft, as well as some academics, authors, legal scholars, states and foreign governments. The Justice Department opposed the deal, fearing that it would give Google a monopoly over millions of so-called orphan works, books whose right holders are unknown or cannot be found.
{ NY Times | Continue reading }
books, economics, law, technology | March 22nd, 2011 7:00 pm
economics, technology | March 22nd, 2011 7:00 pm

Researchers who have spent the last two years studying the security of car computer systems have revealed that they can take control of vehicles wirelessly.
The researchers were able to control everything from the car’s brakes to its door locks to its computerized dashboard displays by accessing the onboard computer through GM’s OnStar and Ford’s Sync, as well as through the Bluetooth connections intended for making hands-free phone calls. They presented their findings this week.
{ Technology Review | Continue reading }
motorpsycho, technology, transportation, uh oh | March 21st, 2011 4:47 pm

The US military is developing software that will let it secretly manipulate social media sites such as Facebook and Twitter by using fake online personas to influence internet conversations and spread pro-American propaganda.
A Californian corporation has been awarded a contract with United States Central Command (Centcom), which oversees US armed operations in the Middle East and Central Asia, to develop what is described as an “online persona management service” that will allow one US serviceman or woman to control up to 10 separate identities based all over the world.
{ Guardian | Continue reading }
painting { Jean Leon Gerome }
U.S., social networks | March 17th, 2011 4:40 pm

In 1978, the NASA scientist Donald Kessler predicted that a collision between two pieces of space junk could trigger a cascade of further impacts, creating dangerously large amounts of debris.
Kessler pointed out that when the rate at which debris forms is faster than the rate at which it de-orbits, then the Earth would become surrounded by permanent belts of junk, a scenario now known as the Kessler syndrome.
By some estimates, the Kessler syndrome has already become a reality. In January 2009, a collision between the Iridium 33 and Cosmos 2251 satellites created just this kind of cascade. Two years earlier, the Chinese military tested an anti-satellite weapon by destroying one of its own satellites called Fengyun 1C. Both incidents took place at altitudes of about 800 km. (…)
Various ideas have been floated for removing space junk, most of them hugely expensive.
Today, James Mason at NASA Ames Research Center near Palo Alto and a few buddies describe a much cheaper option. Their idea is to zap individual pieces of junk with a ground-based laser, thereby slowing them down so that they eventually de-orbit.
{ The Physics arXiv Blog | Continue reading }
space, technology | March 14th, 2011 5:30 pm

{ Edward Weston, White Sands, 1946 }
related { The Cloud: Battle of the Tech Titans. Amazon, Google, and Microsoft are going up against traditional infrastructure makers like IBM and HP as businesses move their most important work to cloud computing, profoundly changing how companies buy computer technology. | Business week | full story }
economics, google, photogs, technology | March 14th, 2011 5:10 pm

Dazzle camouflage, also known as Razzle Dazzle or Dazzle painting, was a camouflage paint scheme used on ships, extensively during World War I and to a lesser extent in World War II. Credited to artist Norman Wilkinson, it consisted of a complex pattern of geometric shapes in contrasting colours, interrupting and intersecting each other.
{ Wikipedia | Continue reading | more photos }

Face-detection software is everywhere. Defeat it with some artfully-applied, avant-garde face makeup called CV Dazzle.
CV Dazzle is named after the ingenious warship-camouflage designs deployed during World War I. Rather than actually hiding military vessels, the bold, jagged paint jobs made it difficult for naval rangefinders to discern details about the ship’s size, heading, armament, and so forth. Or at least, that was the idea — unlike Harvey’s digital version, the original Dazzle’s effectiveness was never proven. Of course, CV Dazzle benefits from the fact that face-detection software is much stupider than WWI seamen: you only have to apply a few strokes of face-paint to confuse it, rather than coat your whole kisser.
{ Fast Company| Continue reading }
flashback, guide, technology, visual design | March 10th, 2011 5:25 pm

We are now looking at a situation where electronic communication is with us at all times and the boundaries between internet and real life communication are becoming increasingly blurred. (…)
Facebook users have a mixture of what would be termed as weak ties (friends a user has a marginal link to), and close ties (friends with whom they maintain a close relationship) in one place. Developing weak ties is one of the primary sources for people using Facebook. Romantic relationships may only represent a small part of a person’s Facebook usage it is nevertheless the most public place a couple will represent themselves. Muize found there was a correlation between the time a user spends on Facebook and relationship jealousy, while Boyd and Lewis showed Facebook to be an environment that can impact upon an intimate relationship.
Much of the literature, however, has focused on the value of maintaining weak ties and enhancing social capital. This paper will take a different stance and compare how certain rituals on Facebook can impact a person’s intimate relationships on the offline environment.
{ Journal of Comparative Research in Anthropology and Sociology, | PDF }
image { Nam June Paik, Homage to Stanley Brown, 1984 | Stedelijk Museum }
relationships, social networks | March 7th, 2011 6:42 pm

{ Our results show that dog and cat owners use these sites quite differently. While dog owners focus on their relationship with their pets and looking for advice, cat owners tend to use the site more to build community. Both results show that these pet social networks are already being used to help support the human–animal bond online. | First Monday | full story }
dogs, relationships, technology | March 7th, 2011 6:20 pm
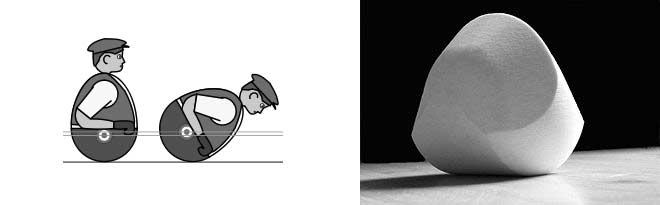
A Gömböc (pronounced [ˈɡømbøts], simplified to Gomboc) is a convex three-dimensional homogeneous body which, when resting on a flat surface, has just one stable and one unstable point of equilibrium. Its existence was conjectured by Russian mathematician Vladimir Arnold in 1995 and proven in 2006 by Hungarian scientists Gábor Domokos and Péter Várkonyi. (…)
The balancing properties of the Gömböc are associated with the “righting response”, their ability to turn back when placed upside down, of shelled animals such as turtles and beetles.
{ Wikipedia | Continue reading | Thanks to James T. }
mathematics, technology | March 3rd, 2011 1:02 pm























